Google Pixel returns to NBA All-Star Weekend in San Francisco, California, with two interactive fan experiences.First, check out the Google Pixel House where you can dem…
Author Archives: [email protected]
Microsoft Edge is very pleased to announce our participation in the fifth edition of the Interop project: Interop 2025. We’re joining forces with our colleagues at Apple, Bocoup, Igalia, Google, and Mozilla, to improve interoperability on the web platform. Interoperability matters because it ensures that the code you write for the web will work the […]
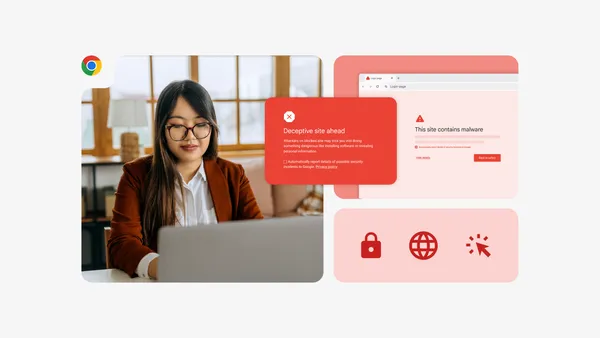
Learn how Chrome Enterprise offers an extra layer of protection and control businesses can adapt to meet their needs.
A widespread phishing campaign has been observed leveraging bogus PDF documents hosted on the Webflow content delivery network (CDN) with an aim to steal credit card information and commit financial fraud. “The attacker targets victims searching for documents on search engines, resulting in access to malicious PDF that contains a CAPTCHA image embedded with a […]
The post Our new partnership with WSP will accelerate digital and AI transformation across the Architecture, Engineering, and Construction industry. appeared first on Stories.
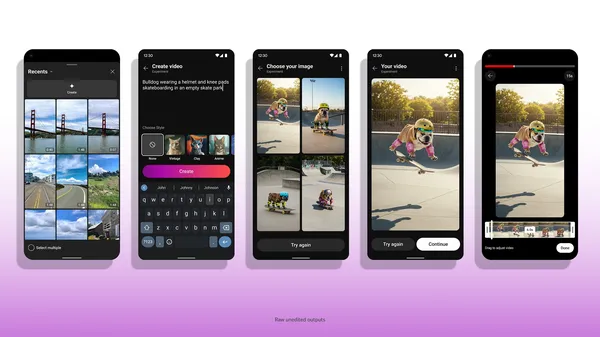
In December, we announced Veo 2, our latest video generation model that creates incredibly high-quality videos in a wide range of subjects and styles. Now, you can try i…
A China-based threat actor, tracked as Emperor Dragonfly and commonly associated with cybercriminal endeavors, has been observed using in a ransomware attack a toolset previously attributed to espionage actors. […]
A nation-state threat actor with ties to North Korea has been linked to an ongoing campaign targeting South Korean business, government, and cryptocurrency sectors. The attack campaign, dubbed DEEP#DRIVE by Securonix, has been attributed to a hacking group known as Kimsuky, which is also tracked under the names APT43, Black Banshee, Emerald Sleet, Sparkling Pisces, […]
Google is introducing a new AI-driven feature to help protect younger users across its platforms, including YouTube. The post Google will use AI to determine if you’re an underage user appeared first on MSPoweruser.
Ever felt like your team is stuck in a constant battle? Developers rush to add new features, while security folks worry about vulnerabilities. What if you could bring both sides together without sacrificing one for the other? We invite you to our upcoming webinar, “Opening the Fast Lane for Secure Deployments.” This isn’t another tech […]