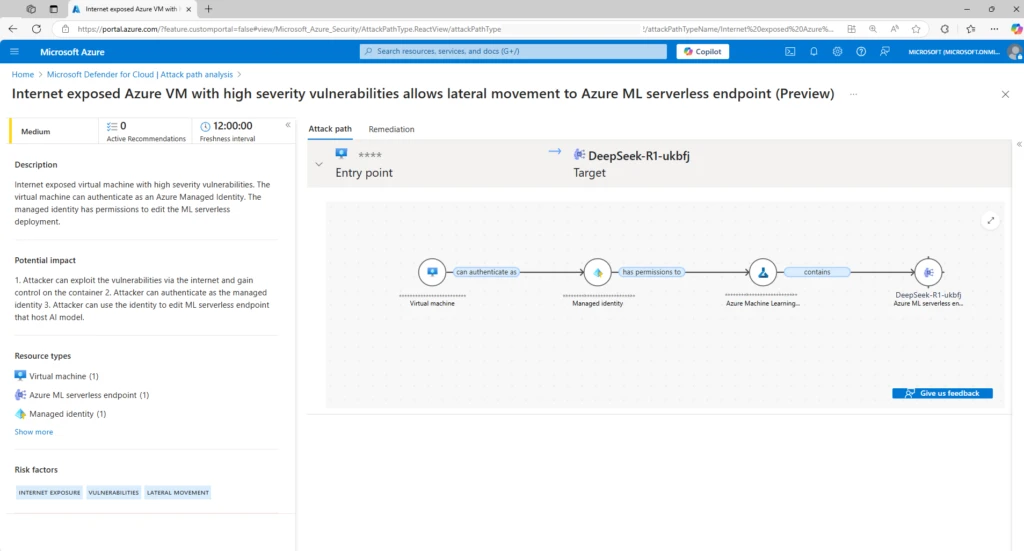
South Korea has formally suspended new downloads of Chinese artificial intelligence (AI) chatbot DeepSeek in the country until the service makes changes to its mobile apps to comply with data protection regulations. Downloads have been paused as of February 15, 2025, 6:00 p.m. local time, the Personal Information Protection Commission (PIPC) said in a statement. […]
Author Archives: [email protected]
More ASUS customers can now install Windows 11 24H2 after applying a BIOS update that resolves blue screen of death (BSOD) issues acknowledged in October. […]
Cyber threats evolve—has your defense strategy kept up? A new free guide available here explains why Continuous Threat Exposure Management (CTEM) is the smart approach for proactive cybersecurity. This concise report makes a clear business case for why CTEM’s comprehensive approach is the best overall strategy for shoring up a business’s cyber defenses in the […]
Welcome to this week’s Cybersecurity News Recap. Discover how cyber attackers are using clever tricks like fake codes and sneaky emails to gain access to sensitive data. We cover everything from device code phishing to cloud exploits, breaking down the technical details into simple, easy-to-follow insights. ⚡ Threat of the Week Russian Threat Actors Leverage […]
Cybersecurity researchers have shed light on a new Golang-based backdoor that uses Telegram as a mechanism for command-and-control (C2) communications. Netskope Threat Labs, which detailed the functions of the malware, described it as possibly of Russian origin. “The malware is compiled in Golang and once executed it acts like a backdoor,” security researcher Leandro Fróes […]
Google Chrome has updated the existing “Enhanced protection” feature with AI to offer “real-time” protection against dangerous websites, downloads and extensions. […]
A new malware called FinalDraft has been using Outlook email drafts for command-and-control communication in attacks against a ministry in a South American country. […]
An active campaign from a threat actor potentially linked to Russia is targeting Microsoft 365 accounts of individuals at organizations of interest using device code phishing. […]
Google is working on a new security feature for Android that blocks device owners from changing sensitive settings when a phone call is in progress. Specifically, the in-call anti-scammer protections include preventing users from turning on settings to install apps from unknown sources and granting accessibility access. The development was first reported by Android Authority. […]
A successful AI transformation starts with a strong security foundation. With a rapid increase in AI development and adoption, organizations need visibility into their emerging AI apps and tools. Microsoft Security provides threat protection, posture management, data security, compliance, and governance to secure AI applications that you build and use. These capabilities can also be […]