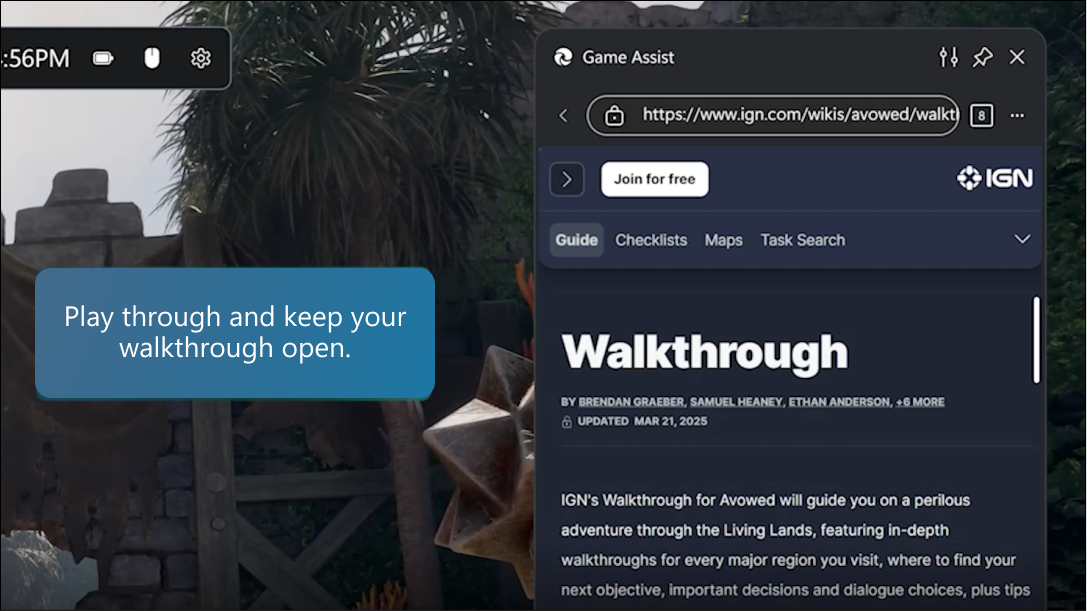
This year, at Microsoft Build, we introduced new AI tools and capabilities designed to empower every software developer to become an AI developer.
The post New AI innovations that are redefining the future for software companies appeared first on Microsoft Azure Blog.