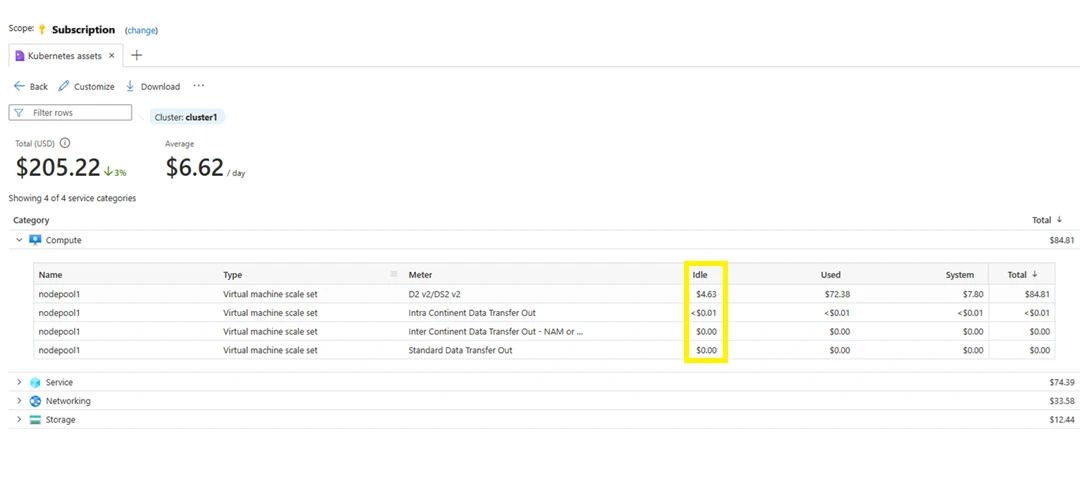
In this article Optimizing AKS (Azure Kubernetes Service) costs AWS (Azure Web Services) connector deprecation Exchange of Azure OpenAI Service Provisioned Reservations Help shape the future of cost reporting Documentation updates What’s next for Cost Management? Whether you’re a new student, a thriving startup, or the largest enterprise, you have financial constraints, and you need […]
Author Archives: [email protected]
Cybersecurity researchers have warned of a malicious campaign targeting users of the Python Package Index (PyPI) repository with bogus libraries masquerading as “time” related utilities, but harboring hidden functionality to steal sensitive data such as cloud access tokens. Software supply chain security firm ReversingLabs said it discovered two sets of packages totaling 20 of them. […]
A large-scale Coinbase phishing attack poses as a mandatory wallet migration, tricking recipients into setting up a new wallet with a pre-generated recovery phrase controlled by attackers. […]
A clever malware deployment scheme first spotted in targeted attacks last year has now gone mainstream. In this scam, dubbed “ClickFix,” the visitor to a hacked or malicious website is asked to distinguish themselves from bots by pressing a combination of keyboard keys that causes Microsoft Windows to download password-stealing malware. ClickFix attacks mimic the […]
Microsoft says it partially mitigated a week-long Exchange Online outage causing delays or failures when sending or receiving email messages. […]
Over the coming months, we’ll be upgrading users on mobile devices from Google Assistant to Gemini.
The Black Basta ransomware operation created an automated brute-forcing framework dubbed ‘BRUTED’ to breach edge networking devices like firewalls and VPNs. […]
Cisco has patched a denial of service (DoS) vulnerability that lets attackers crash the Border Gateway Protocol (BGP) process on IOS XR routers with a single BGP update message. […]
A 51-year-old dual Russian and Israeli national who is alleged to be a developer of the LockBit ransomware group has been extradited to the United States, nearly three months after he was formally charged in connection with the e-crime scheme. Rostislav Panev was previously arrested in Israel in August 2024. He is said to have been […]
The GSM Association (GSMA) has formally announced support for end-to-end encryption (E2EE) for securing messages sent via the Rich Communications Services (RCS) protocol, bringing much-needed security protections to cross-platform messages shared between Android and iOS platforms. To that end, the new GSMA specifications for RCS include E2EE based on the Messaging Layer Security (MLS) protocol