Two now-patched security flaws impacting Cisco Smart Licensing Utility are seeing active exploitation attempts, according to SANS Internet Storm Center. The two critical-rated vulnerabilities in question are listed below – CVE-2024-20439 (CVSS score: 9.8) – The presence of an undocumented static user credential for an administrative account that an attacker could exploit to log in […]
Author Archives: [email protected]
Veeam has patched a critical remote code execution vulnerability tracked as CVE-2025-23120 in its Backup & Replication software that impacts domain-joined installations. […]
CISA has warned U.S. federal agencies to secure their networks against attacks exploiting a high-severity vulnerability in NAKIVO’s Backup & Replication software. […]
Two malicious VSCode Marketplace extensions were found deploying in-development ransomware from a remote server, exposing critical gaps in Microsoft’s review process. […]
Attackers have started targeting Cisco Smart Licensing Utility (CSLU) instances unpatched against a vulnerability exposing a built-in backdoor admin account. […]
How and when you should switch to post-quantum Written by Cory Missimore of the CSA Quantum-Safe Security Working Group. Reviewed by Bruno Huttner, Mehak Kalsi, and Mahesh Adulla. NIST is helping companies and governments prepare for PQC As quantum computing technology continues to advance, so does the urgency for organizations to rethink their approach to cybersecurity. Many […]
Security researchers have linked a new backdoor dubbed Betruger, deployed in several recent ransomware attacks, to an affiliate of the RansomHub operation. […]
There are tons of new features to check out in the Gemini app, from personalization to real-time collaboration. In the latest episode of the Google AI: Release Notes pod…
The UK’s National Cyber Security Centre (NCSC) has published specific timelines on migrating to post-quantum cryptography (PQC), dictating that critical organizations should complete migration by 2035. […]
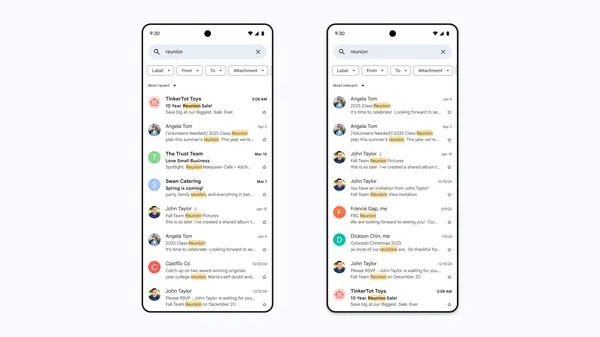
If you’ve ever struggled with finding information in your overflowing inbox, you’re not alone. That’s why Gmail is rolling out a smarter search feature powered by AI to …