Author Archives: [email protected]
Defend your AI systems with Prompt Shields—a unified API that analyzes inputs to your LLM-based solution to guard against direct and indirect threats.
The post Enhance AI security with Azure Prompt Shields and Azure AI Content Safety appeared first on Microsoft Azure Blog.
Hello Windows Insiders,
We’re excited to announce an update to the Microsoft Photos app, now rolling out on Windows 11 across all Insider channels. This release brings powerful new features on Copilot+ PCs, designed to help you enhance, rediscover
The post AI-powered Relight and Search now available in Microsoft Photos appeared first on Windows Blog.
 As we shared at I/O, the Gemini app is getting more personal, proactive and powerful. Starting today, we’re rolling out scheduled actions in the Gemini app, a new featur…
As we shared at I/O, the Gemini app is getting more personal, proactive and powerful. Starting today, we’re rolling out scheduled actions in the Gemini app, a new featur…The campaign, according to CloudSEK, has been found to leverage typosquat domains mimicking U.S.-based telecom provider Spectrum.
“macOS users are served a
 The Google Play Books team released a curated list of the books they read and loved so far this year. From thrilling fantasy epics to thought-provoking nonfiction to bon…
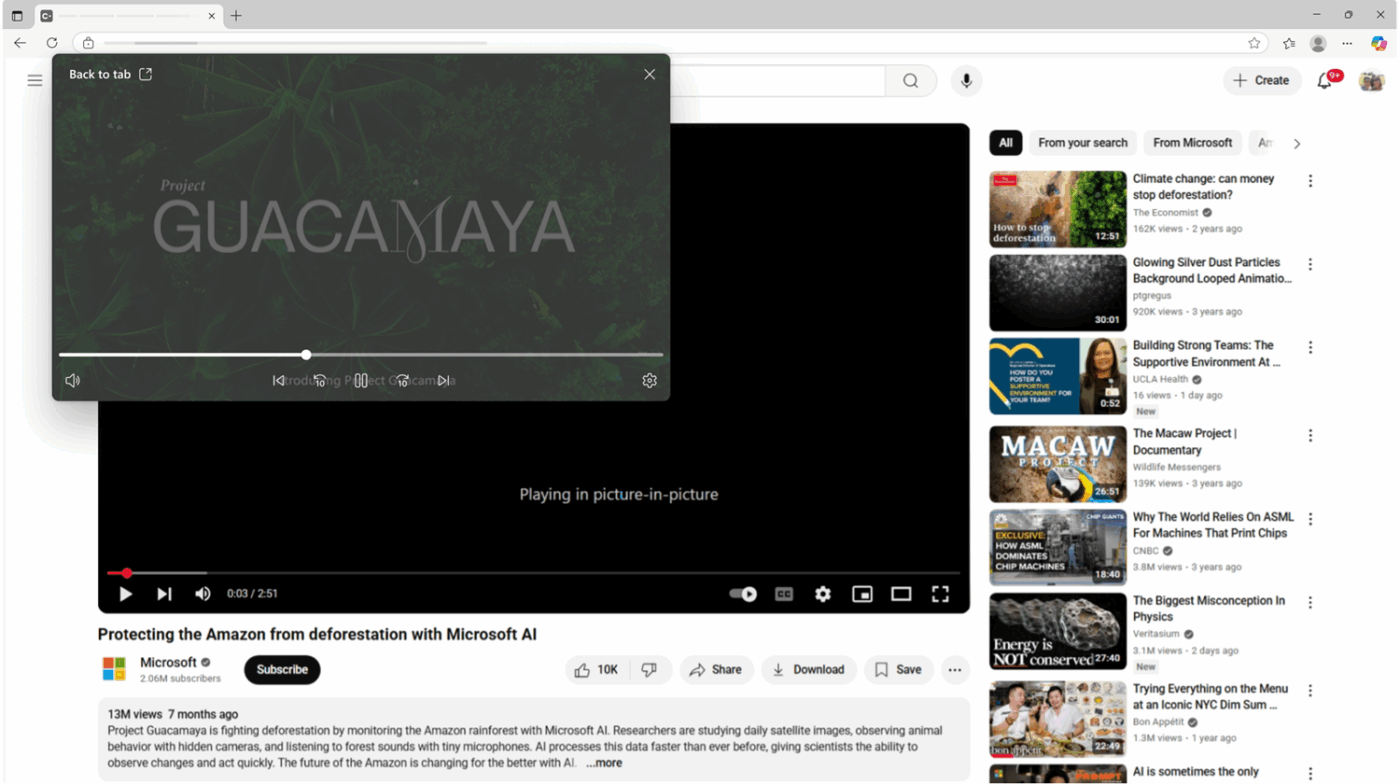
The Google Play Books team released a curated list of the books they read and loved so far this year. From thrilling fantasy epics to thought-provoking nonfiction to bon…At Microsoft Edge, we’re committed to delivering the best browsing experience possible. Our users have been asking for more controls and flexibility in our picture-in-picture feature. Today, we’re excited to announce that we’re rolling out a signific
The post Debuting new enhanced controls for picture-in-picture in Microsoft Edge appeared first on Windows Blog.