Microsoft is testing a dedicated page in Windows Settings for quick machine recovery, which will provide users with additional configuration options. […]
Monthly Archives: June 2025
Two malicious RubyGems packages posing as popular Fastlane CI/CD plugins redirect Telegram API requests to attacker-controlled servers to intercept and steal data. […]
Threat hunters are alerting to a new campaign that employs deceptive websites to trick unsuspecting users into executing malicious PowerShell scripts on their machines and infect them with the NetSupport RAT malware.
The DomainTools Investigations (DTI) team said it identified “malicious multi-stage downloader Powershell scripts” hosted on lure websites that masquerade as Gitcode and DocuSign.
“
The DomainTools Investigations (DTI) team said it identified “malicious multi-stage downloader Powershell scripts” hosted on lure websites that masquerade as Gitcode and DocuSign.
“
Mozilla has developed a new security feature for its add-on portal that helps block Firefox malicious extensions that drain cryptocurrency wallets. […]
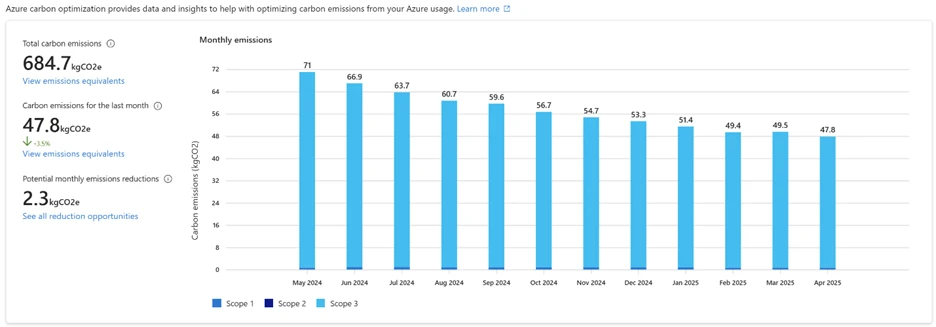
Nobody wants a surprise when it comes to the bill, and this is where Microsoft Cost Management comes in.
The post Microsoft Cost Management updates—May 2025 appeared first on Microsoft Azure Blog.
Scattered Spider isn’t one group — it’s an identity-first threat model evolving fast. From vishing to AiTM phishing, they’re exploiting MFA gaps to hijack the cloud. Watch the Push Security webinar to learn how their identity-based tactics work — and how to stop them. […]
CISA is alerting federal agencies in the U.S. of hackers exploiting a recently patched ScreenConnect vulnerability that could lead to executing remote code on the server. […]
Fashion retail giant Victoria’s Secret has delayed its first quarter 2025 earnings release because of ongoing corporate system restoration efforts following a May 24 security incident. […]
Cybersecurity researchers have disclosed details of a critical security flaw in the Roundcube webmail software that has gone unnoticed for a decade and could be exploited to take over susceptible systems and execute arbitrary code.
The vulnerability, tracked as CVE-2025-49113, carries a CVSS score of 9.9 out of 10.0. It has been described as a case of post-authenticated remote code execution via
The vulnerability, tracked as CVE-2025-49113, carries a CVSS score of 9.9 out of 10.0. It has been described as a case of post-authenticated remote code execution via
Written by Olivia Rempe, Community Engagement Manager, Cloud Security Alliance.
There’s no denying it—Large Language Models (LLMs) have changed the game for software development.
They can autocomplete boilerplate, refactor legacy functions, and even generate entire microservices with a well-crafted prompt. But as tempting as it is to let that generated code run, here’s a word of caution:
Letting an LLM write code is powerful.
Letting it execute code? That’s dangero…