Monthly Archives: June 2025
Cloud security firm Wiz, which is tracking the activity under the name JINX-0132, said the attackers are exploiting a wide range of known misconfigurations and
A brief description of the three flaws is as follows –
CVE-2024-13915 (CVSS score: 6.9) – A pre-installed “com.pri.factorytest” application on Ulefone and
Imagine there’s no error
It’s easy if you try
No conflict in the circuits
Just agents standing by
Imagine all the agents
Talking all the time…
Imagine there’s no failure
It isn’t hard to do
No warnings or exceptions
No oversight from you
Imagine all the agents
Working hand in hand…
You may say I’m a dreamer
But I’m not the only one
I hope we learn to listen
Before the chaos has begun
…
The flaws in question, which were responsibly disclosed to the company by the Google Android Security team, are listed below –
CVE-2025-21479 and CVE-2025-21480 (CVSS score: 8.6) – Two incorrect authorization vulnerabilities in the Graphics
Written by John Filitz.
SaaS applications have become the backbone of productivity and collaboration, but the convenience of cloud-based tools brings significant security challenges that often fly under the radar. As security leaders, it’s crucial to understand the risks of data sharing in SaaS to protect your organization’s most valuable assets.
Data from our recent survey shows that 58% of organizations experienced at least one SaaS-…
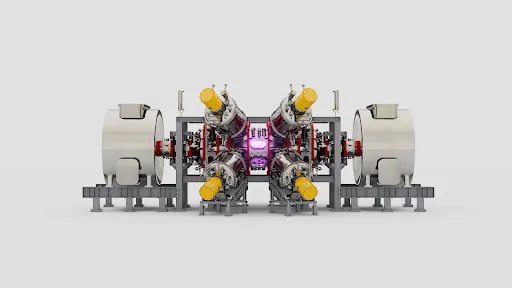
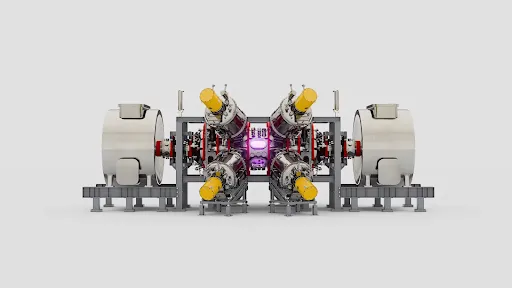
 Starting in 2015, Google Research collaborated with TAE, applying AI to drive significant improvements in plasma temperature and lifetime, and help them better understan…
Starting in 2015, Google Research collaborated with TAE, applying AI to drive significant improvements in plasma temperature and lifetime, and help them better understan… Starting in 2015, Google Research collaborated with TAE, applying AI to drive significant improvements in plasma temperature and lifetime, and help them better understan…
Starting in 2015, Google Research collaborated with TAE, applying AI to drive significant improvements in plasma temperature and lifetime, and help them better understan…