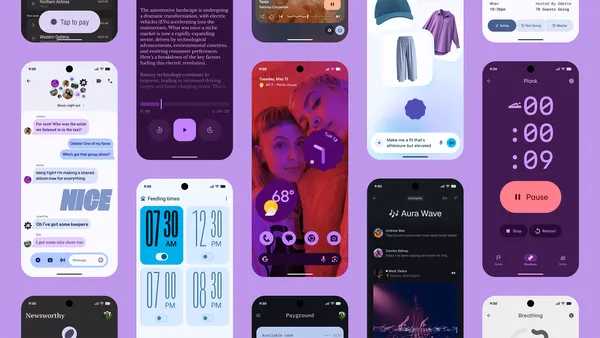
Learn more about Material 3 Expressive, the new design for Android and Wear OS devices coming later this year to Pixel devices first.
Monthly Archives: May 2025
Over the last few years, we’ve been focused on improving how people connect, no matter what phone they have. That’s why we helped make RCS the messaging standard for And…
At The Android Show: I/O Edition, we shared what’s new in the Android ecosystem: From new design to Gemini to safety and more.
Fortinet released security updates to patch a critical remote code execution vulnerability exploited as a zero-day in attacks targeting FortiVoice enterprise phone systems. […]
Ivanti has released security updates for its Neurons for ITSM IT service management solution that mitigate a critical authentication bypass vulnerability. […]
A recently disclosed critical security flaw impacting SAP NetWeaver is being exploited by multiple China-nexus nation-state actors to target critical infrastructure networks. “Actors leveraged CVE-2025-31324, an unauthenticated file upload vulnerability that enables remote code execution (RCE),” EclecticIQ researcher Arda Büyükkaya said in an analysis published today. Targets of the campaign
A new “Branch Privilege Injection” flaw in all modern Intel CPUs allows attackers to leak sensitive data from memory regions allocated to privileged software like the operating system kernel. […]
Cybersecurity researchers have discovered a malicious package on the Python Package Index (PyPI) repository that purports to be an application related to the Solana blockchain, but contains malicious functionality to steal source code and developer secrets. The package, named solana-token, is no longer available for download from PyPI, but not before it was downloaded 761 […]
Microsoft has backtracked on its plan to end support for Office apps on Windows 10 later this year and announced that it will continue providing security updates for three more years, until 2028. […]
Red teams uncover what others miss — but they can’t be everywhere, all the time. Adversarial Exposure Validation combines BAS + Automated Pentesting to extend red team impact, uncover real attack paths, and validate defenses continuously. Learn more from Picus Security on how AEV can help protect your network. […]