Google’s AI Works report shares how the UK can double AI usage, narrow the AI adoption gap, and boost worker productivity.
Monthly Archives: April 2025
We announced new partnerships and investment in the fight against scams at the recent Online Safety Dialogue 2025.
Russian threat actors have been abusing legitimate OAuth 2.0 authentication workflows to hijack Microsoft 365 accounts of employees of organizations related to Ukraine and human rights. […]
In a recent espionage campaign, the infamous North Korean threat group Lazarus targeted multiple organizations in the software, IT, finance, and telecommunications sectors in South Korea. […]
Microsoft says it mitigated a known issue in one of its machine learning (ML) models that mistakenly flagged Adobe emails in Exchange Online as spam. […]
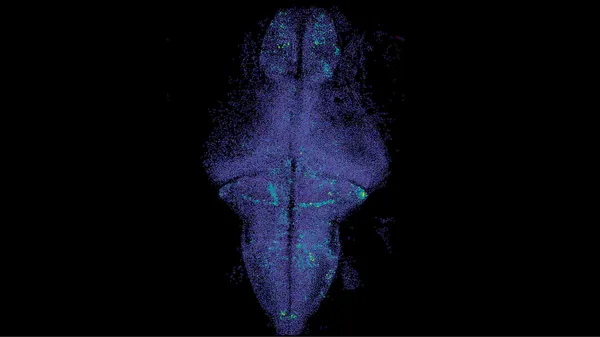
AI could one day help neuroscientists predict activity in the human brain, just like language models can predict the next word in a sentence.After more than a decade of …
A ransomware attack in January at Frederick Health Medical Group, a major healthcare provider in Maryland, has led to a data breach affecting nearly one million patients. […]
Our latest Google Workspace feature drop is here with new tools to help you collaborate, stay on top of your to-do list and do your best work. Plus, this latest update h…
Microsoft announced an increase in bug bounty payouts to $30,000 for AI vulnerabilities found in Dynamics 365 and Power Platform services and products. […]