As part of its efforts to add AI everywhere, Microsoft is now bringing AI features to the popular Paint and Notepad apps on Windows 11. […]
Monthly Archives: November 2024
The Federal Bureau of Investigation (FBI) is urging police departments and governments worldwide to beef up security around their email systems, citing a recent increase in cybercriminal services that use hacked police email accounts to send unauthorized subpoenas and customer data requests to U.S.-based technology companies. In an alert (PDF) published this week, the FBI […]
Microsoft has confirmed that last month’s Windows security updates are breaking SSH connections on some Windows 11 22H2 and 23H2 systems. […]
A malicious Python package named ‘fabrice’ has been present in the Python Package Index (PyPI) since 2021, stealing Amazon Web Services credentials from unsuspecting developers. […]
Palo Alto Networks on Friday issued an informational advisory urging customers to ensure that access to the PAN-OS management interface is secured because of a potential remote code execution vulnerability. “Palo Alto Networks is aware of a claim of a remote code execution vulnerability via the PAN-OS management interface,” the company said. “At this time, […]
The 36-year-old founder of the Bitcoin Fog cryptocurrency mixer has been sentenced to 12 years and six months in prison for facilitating money laundering activities between 2011 and 2021. Roman Sterlingov, a dual Russian-Swedish national, pleaded guilty to charges of money laundering and operating an unlicensed money-transmitting business earlier this March. The U.S. Department of […]
In an era defined by the transformative power of AI, industries are reimagining the possibilities of predictive analytics, automation, and real-time decision-making. AI is now ubiquitous, reshaping sectors from retail and finance to healthcare and biotechnology. While new applications harness AI’s potential, it’s the evolution of existing applications through generative AI methodologies that drives exponential […]
AI success depends on multiple factors, but the key to innovation is the quality and accessibility of an organization’s proprietary data. I sat down with Teresa Tung to discuss the opportunities of proprietary data and why it is so critical to value creation with AI. Tung is a researcher whose work spans breakthrough cloud technologies, […]
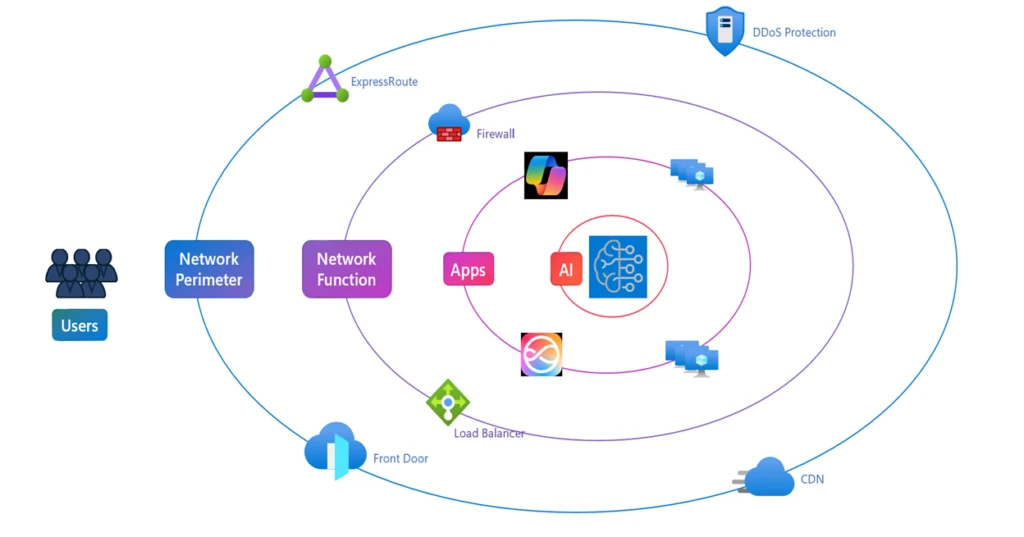
As organizations embrace AI transformation, they are searching for next-generation applications that deliver real business value. McKinsey estimates that 67% of organizations will invest more in AI over the next three years.1 And software as a service (SaaS) spend is estimated to hit USD232 billion in 2024, up 18% from the prior year.2 There has been a […]
Over 60,000 customers including AT&T, H&R Block, Volvo, Grammarly, Harvey, Leya, and more leverage Microsoft Azure AI to drive AI transformation. We are excited to see the growing adoption of AI across industries and businesses small and large. This blog summarizes new capabilities across Azure AI portfolio that provide greater choice and flexibility to build […]