A Mullvad VPN user has discovered that Android devices leak DNS queries when switching VPN servers even though the “Always-on VPN” feature was enabled with the “Block connections without VPN” option. […]
Monthly Archives: May 2024
The NSA and FBI warned that the APT43 North Korea-linked hacking group exploits weak email Domain-based Message Authentication Reporting and Conformance (DMARC) policies to mask spearphishing attacks. […]
Google has rolled back a recent release of its reCaptcha captcha script after a bug caused the service to no longer work on Firefox for Windows. […]
Hello Windows Insiders, today we are releasing Windows 11 Insider Preview Build 26120.461 (KB5037009) to the Dev Channel. Windows Insiders in the Dev Channel will now receive updates based on Windows 11, version 24H2 via an enablement package (Build 26120.xxxx). For Insiders in the Dev Channel who want to be the first to get features gradually […]
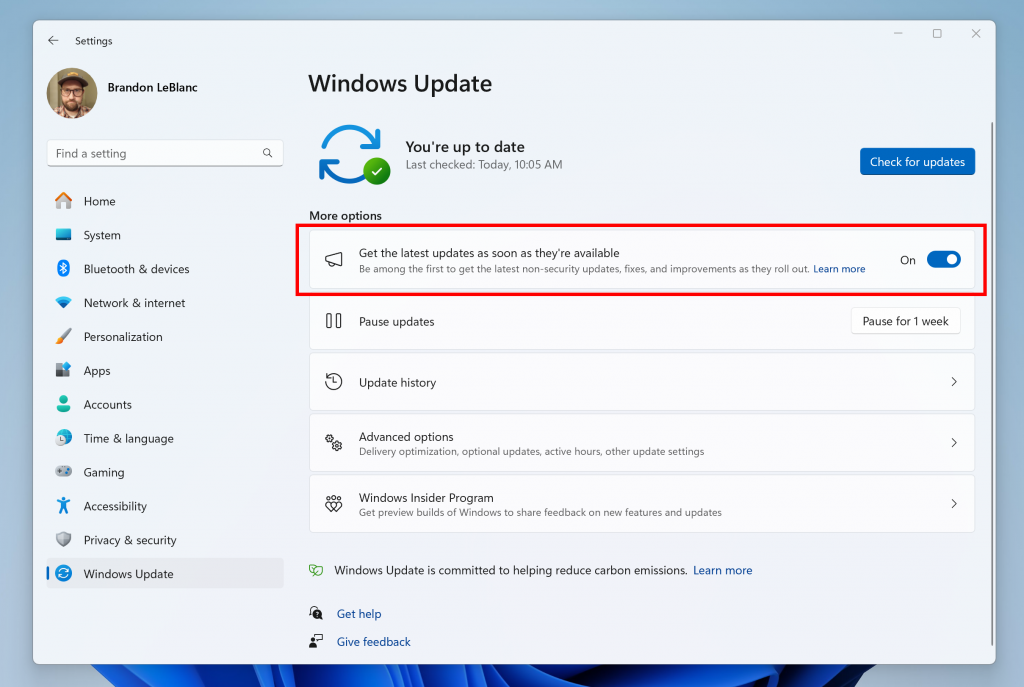
Hello Windows Insiders, today we are releasing Windows 11 Insider Preview Build 22635.3570 (KB5037008) to the Beta Channel. REMINDER: All Windows Insiders in the Beta Channel will now be on the same build (Build 22635.xxxx) via an enablement package. For Windows Insiders in the Beta Channel who want to be the first to get features gradually […]
NATO and the European Union, with international partners, formally condemned a long-term cyber espionage campaign against European countries conducted by the Russian threat group APT28. […]
Microsoft announced that Windows users can now log into their Microsoft consumer accounts using a passkey, allowing users to authenticate using password-less methods such as Windows Hello, FIDO2 security keys, biometric data (facial scans or fingerprints), or device PINs. […]
Originally published by CXO REvolutionaries.Written by Ben Corll, CISO in Residence, Zscaler.In early 2024, I had the privilege of teaching a SANS leadership course in New Orleans. The food was amazing, as expected. What I didn’t expect was the sheer number of operational technology (OT) security professionals who would be in attendance. As I attended […]
In today’s rapidly evolving digital landscape, the threat of Distributed Denial of Service (DDoS) attacks looms more significant than ever. As these cyber threats grow in sophistication, understanding and countering them becomes crucial for any business seeking to protect its online presence. To address this urgent need, we are thrilled to announce our upcoming webinar, […]
Threat actors have been increasingly weaponizing Microsoft Graph API for malicious purposes with the aim of evading detection. This is done to “facilitate communications with command-and-control (C&C) infrastructure hosted on Microsoft cloud services,” the Symantec Threat Hunter Team, part of Broadcom, said in a report shared with The Hacker News.