The post Today we announced our largest investment in our nearly three decades in Indonesia, as we partner to advance the country’s cloud and AI ambitions, and help Indonesia thrive in this new era. appeared first on Stories.
Monthly Archives: April 2024
I explored the web and tried over 30 apps to choose the best AudioBoom downloader. Below are the details of my research and some incredible software suggestions! Best AudioBoom Downloader 1. YT Saver YT Saver is a powerful AudioBoom downloader with great features, a user-friendly interface, and incredible download speeds. YT Saver automatically started the […]
UnitedHealth confirms that Change Healthcare’s network was breached by the BlackCat ransomware gang, who used stolen credentials to log into the company’s Citrix remote access service, which did not have multi-factor authentication enabled. […]
Cybersecurity researchers have discovered multiple campaigns targeting Docker Hub by planting millions of malicious “imageless” containers over the past five years, once again underscoring how open-source registries could pave the way for supply chain attacks. “Over four million of the repositories in Docker Hub are imageless and have no content except for the repository
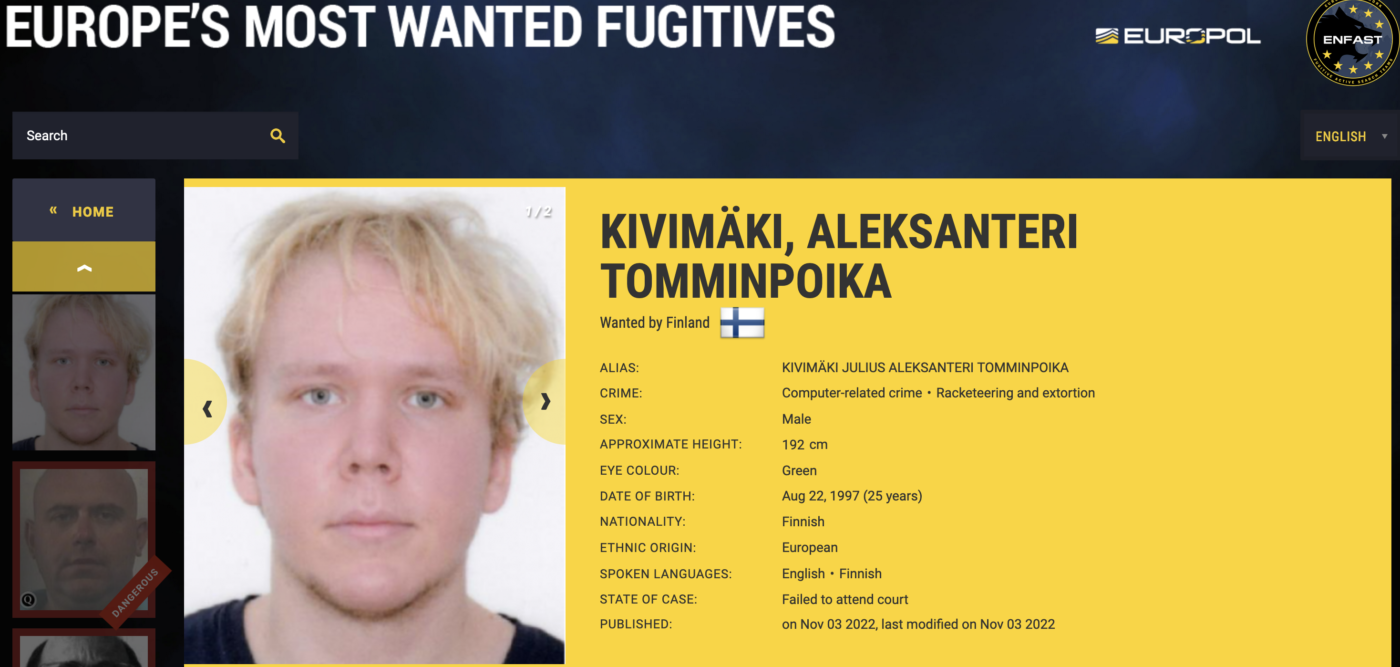
A 26-year-old Finnish man was sentenced to more than six years in prison today after being convicted of hacking into an online psychotherapy clinic, leaking tens of thousands of patient therapy records, and attempting to extort the clinic and patients. On October 21, 2020, the Vastaamo Psychotherapy Center in Finland became the target of blackmail […]
Originally published by Cyera.Healthcare organizations face rising cybersecurity threats looking to exfiltrate patient data. This article explores major healthcare data breaches, the value of stolen medical info, and how data security posture management (DSPM) solutions provide comprehensive data mapping, classification, monitoring, and access controls to secure sensitive health data.The healthcare industry holds a vast amount […]
Finding the best duplicate file finder for Windows 7 can be overwhelming. The good news is that you don’t have to look for these tools alone. I researched, tested, and created a list of the best apps for the job. That way, all you have to do is consider their strengths and weaknesses and pick […]
Originally published by Schellman.Did you recently implement a new artificial intelligence (AI) feature within your application and now your customers are starting to ask for AI-specific penetration tests? Are you curious as to how an assessment like that would work? As with all these exercises, it starts with scoping.Scoping goes beyond just deciding the boundaries […]
Microsoft Edge is announcing the deprecation of legacy CSS properties used for styling websites in high-contrast themes. These legacy properties, the “-ms-high-contrast” media query and “-ms-high-contrast-adjust” property, will be phased out to make space for the more widely adopted “forced colors” standard. High-contrast themes are an accessibility feature that improves text visibility for users with […]
The U.S. government has unveiled new security guidelines aimed at bolstering critical infrastructure against artificial intelligence (AI)-related threats. “These guidelines are informed by the whole-of-government effort to assess AI risks across all sixteen critical infrastructure sectors, and address threats both to and from, and involving AI systems,” the Department of Homeland Security (DHS)&