The WINELOADER backdoor used in recent cyber attacks targeting diplomatic entities with wine-tasting phishing lures has been attributed as the handiwork of a hacking group with links to Russia’s Foreign Intelligence Service (SVR), which was responsible for breaching SolarWinds and Microsoft. The findings come from Mandiant, which said Midnight Blizzard (aka APT29, BlueBravo, or
Monthly Archives: March 2024
Microsoft has released emergency out-of-band (OOB) updates to fix a known issue causing Windows domain controllers to crash after installing the March 2024 Windows Server security updates. […]
Researchers are warning that a notorious hacking group linked to Russia’s Foreign Intelligence Service (SVR) is targeting political parties in Germany for the first time, shifting their focus away from the typical targeting of diplomatic missions. […]
Welcome to Cyber Security Today. This is the Week in Review for the week ending Friday, March 22nd, 2024. I’m Howard Solomon, contributing reporter on cybersecurity for ITWorldCanada.com and TechNewsday.com in the U.S. In a few minutes Terry Cutler of Montreal’s Cyology Labs will be here to talk about recent news. That includes lessons […]
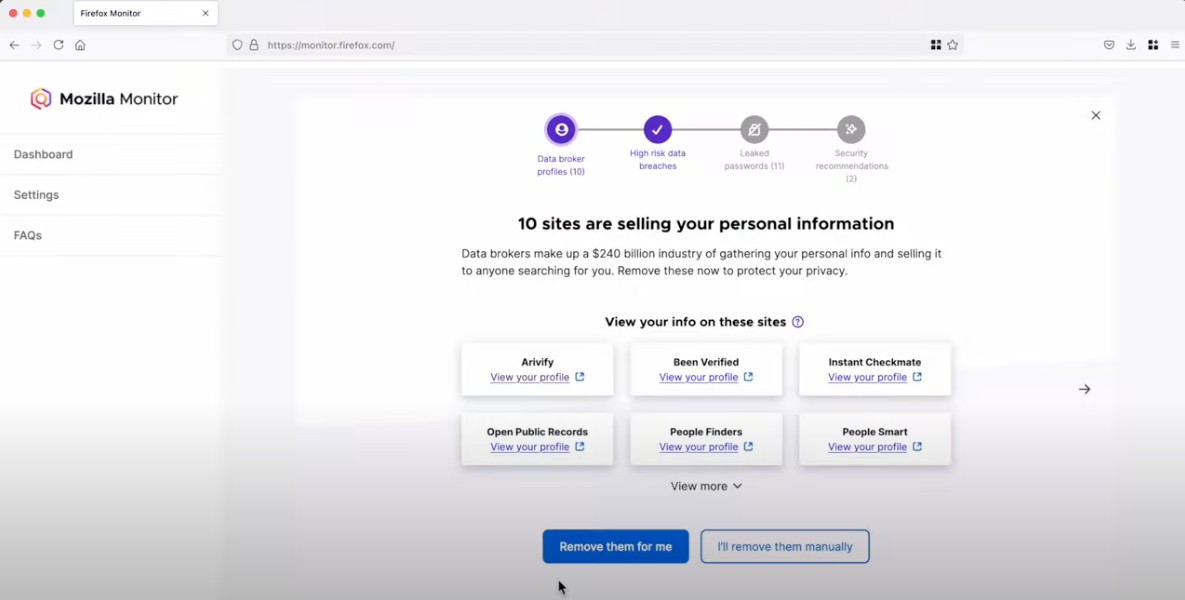
The nonprofit organization that supports the Firefox web browser said today it is winding down its new partnership with Onerep, an identity protection service recently bundled with Firefox that offers to remove users from hundreds of people-search sites. The move comes just days after a report by KrebsOnSecurity forced Onerep’s CEO to admit that he […]
Mozilla has released security updates to fix two zero-day vulnerabilities in the Firefox web browser exploited during the Pwn2Own Vancouver 2024 hacking competition. […]
For this guide, I researched the best TwitCasting downloader apps I could find. Many tools promised results they couldn’t deliver – except these five options. Below are the details of my research and software suggestions, so read on to learn more! 1. YT Saver YT Saver is my top pick for the best TwitCasting downloader […]
The German police have seized infrastructure for the darknet Nemesis Market cybercrime marketplace in Germany and Lithuania, disrupting the site’s operation. […]
In this guide, I’ll show you how to export a Google Maps list to Excel. It’s easier than it sounds. Just follow this simple step-by-step guide. How To Export Google Maps List to Excel Now you’re ready to export your Google Maps lists to Excel. As you can see, all you need to do is […]
Originally published by Astrix.Written by Tal Skverer and Danielle Guetta. “Identity is the new perimeter.” This catch phrase is present in almost every website of identity security vendors, and for a good reason. Human access, more commonly referred to as user access, is an established security program in most organizations – big or small. The […]