Northern Minerals issued an announcement earlier today warning that it suffered a cybersecurity breach resulting in some of its stolen data being published on the dark web. […]
Author Archives: [email protected]
Over the past week, attackers have hijacked high-profile TikTok accounts belonging to multiple companies and celebrities, exploiting a zero-day vulnerability in the social media’s direct messages feature. […]
Today, the FBI issued a warning about scammers using fake remote job ads to steal cryptocurrency from job seekers across the United States while posing as recruiters for legitimate companies. […]
American Radio Relay League (ARRL) has shared more information about a May cyberattack that took its Logbook of the World offline and caused some members to become frustrated over the lack of information. […]
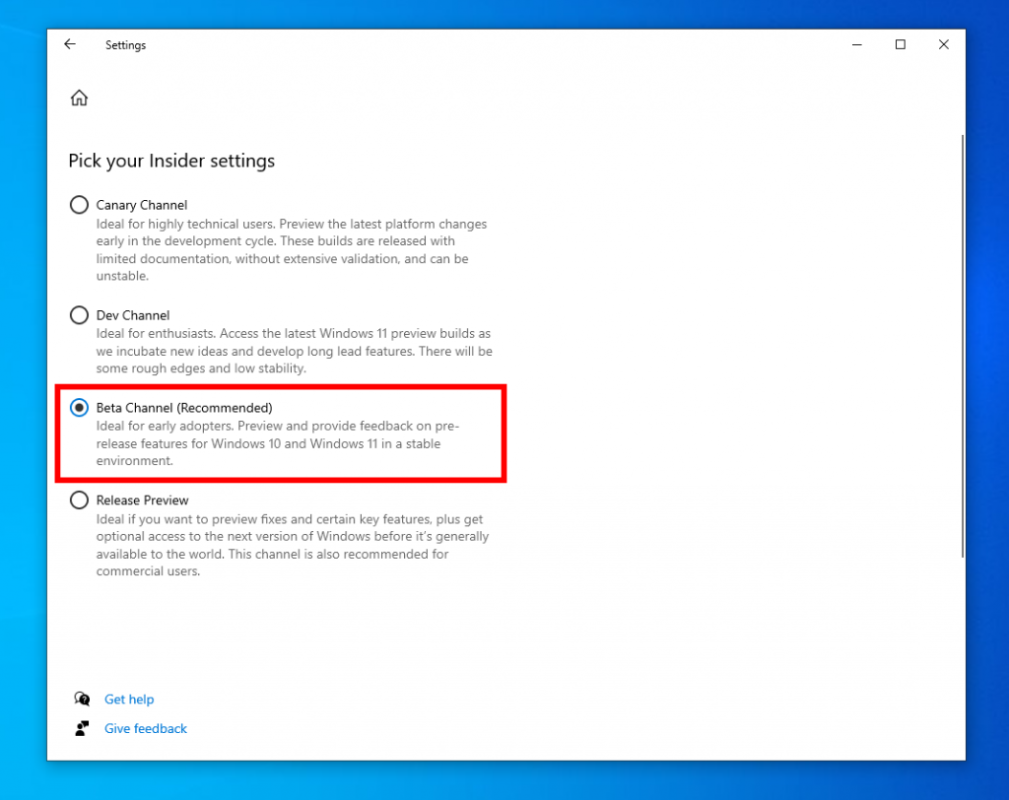
Microsoft has reopened the Windows 10 beta channel and is asking Insiders to join or switch to receive a new beta build in the coming weeks. […]
Cybercriminals are promoting a new phishing kit named ‘V3B’ on Telegram, which currently targets customers of 54 major financial institutes in Ireland, the Netherlands, Finland, Austria, Germany, France, Belgium, Greece, Luxembourg, and Italy. […]
Microsoft is breathing new life into Windows 10 by opening its Beta Channel to Windows Insiders, offering users early access to experimental features and improvements. This move aims to maximize the value of existing Windows 10 PCs while paving the way for a smoother transition to Windows 11. Microsoft announced a significant update to its […]
Microsoft today announced Microsoft Dynamics 365 Contact Center, a contact center solution with generative AI features for every customer engagement channel. Dynamics 365 Contact Center is a standalone Contact Center as a Service (CCaaS) solution and can be connected to any CRMs or custom apps. It will be generally available from July 1st. Since Dynamics […]
Hello Windows Insiders, At the end of last year, we announced a change in approach for Windows 10 to make sure everyone can get the maximum value from their current Windows PC. To bring new features and more improvements to Windows 10 as needed, we need a place to do active feature development with Windows […]
At Computex, NVIDIA celebrated new RTX AI PC laptops from ASUS and MSI that feature its GeForce RTX 4070 Laptop GPUs and power-efficient systems-on-a-chip with Windows 11 AI PC capabilities. These Windows 11 AI PCs* will receive a free update to Copilot+ PC experiences when available. For gamers, creators and developers, these new AI-powered laptops […]